VirtualMV/Internet and Web/Gateway Servers
| Internet and Web | ||
|---|---|---|
| Theory | Introduction | What is HTML? | Client Server ecosystem | Glossary | History and Future | How the Internet works | Types of Website | Markup Languages | Interactive Websites | | |
| Web Tools | Web Browsers | Search Engines (SEO Optimization) | World Wide Web (Hypertext and Page) | Cookies | Email | Discussion Forums | FTP | (SSH, IRC) | |
| Technologies | Connecting | Broadband | Mobile | Web Conferencing | Intranets, Extranets, Tunneling | Gateway Servers | | |
| Issues | Security | Legal (Privacy, Confidentiality, Integrity) | Copyright and Fairdealing | Accessibility | Culture and Netiquette | | |
| Web Site Development | Planning ( Types | For Mobile) | Development (Design Components | Graphic Design) | Programming | Hosting | Marketing and Promotion | Advertising | Business Intelligence | Monitoring and Maintenance (Performance Tuning) | |
| Web Site Management | Roles | Management | User Expectations | Content Management | Site Maintenance | Policies and Guidelines | Promotion | Risk Management | |
Overview
Gateway ServersBy the end of this page you will be able to:
|
Connecting to the Internet, has issues with what content you want filtered (particularly in a business), how multiple requests for the same page is managed. In businesses, these functions are handled by a proxy server.
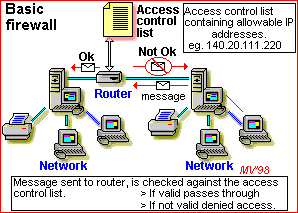
Firewall
Analogy
- When hosting a private party, someone may be stationed at the door to check off names against an invitation list.
Firewall (computing). (2010, November 13)[1]
A firewall is a set of related programs, located at a network gateway server, that protects the resources of a private network from users from other networks. An enterprise with an intranet that allows its workers access to the wider Internet installs a firewall to prevent outsiders from accessing its own private data resources and for controlling what outside resources its own users have access to. A firewall is often installed in a specially designated computer separate from the rest of the network so that no incoming request can get directly at private network resources.
The firewall, working closely with a router program, screens all network packets to determine whether to forward them toward their destination. A firewall also includes or works with a proxy server that makes network requests on behalf of workstation users. There are a number of firewall screening methods. A simple one is to screen requests to make sure they come from acceptable (previously identified) domain names and IP addresses. For mobile users, firewalls allow remote access in to the private network by the use of secure logon procedures and authentication certificates.
Firewalls are usually made up of a combination of;
- Packet filtering
- A router examines each packet, and by following rules programmed into it, accepts messages from certain servers or nodes and drops all others
- Application proxy
- Special purpose software restricts incoming traffic to a specified application, such as email or Lotus Notes. Similarily outgoing traffic can be restricted if it comes from an unauthorised application.
- Circuit level gateway
- This gateway connects an outside TCP/IP port to an internal destination, often a shared resource like a printer. An access control mechanism on the gateway determines whether the user connected to the TCP/IP port is authorised.
- Authentication
- A system gives a user seeking access to the internal network a private key shared with a service on a host. When a key distribution center clears the users key, it unlocks access to the host service.
- Encryption
- Encrypting data streams prevents them from being intercepted and stored as they move along the internet.
Reference : McCann, S. (1998, Nov 16) Quick study - firewalls. , Computerworld NZ 575 . p 30.
Cache
A cache (pronounced CASH) stores temporary local copies of recently accessed documents. Every web page you request is stored in your browser’s cache directory on your hard disk. That way, when you return to a page you’ve recently looked at, the browser can get it from the cache rather than the original server, saving you time and the network the burden of some additional traffic. You can usually vary the size of your cache, depending on your particular browser. The bigger your cache, the longer that documents will be stored before the cache is full and the oldest documents deleted.
Cache Settings in IE6 can be accessed using; Tools | Internet Options then in the Temporary Internet Files select the [Settings] button. It is possible to view your cache by simply exploring the directory. On shared machines you can see what other people have been accessing! There is also software called cache viewers that make navigating and viewing the cache more easy.
As well as your browser`s cache, there are also several levels of cache on the Internet. Many local networks, e.g. companies, institutes or ISPs maintain a local cache often in association with the gateway server, firewall and proxy server. When people within that organisation request a webpage the cache is checked to see whether it has a local copy of the page. If it doesn’t then the original document is retrived from the WWW, and a local copy made for the next time that a user requests that page. Many also have caches - There are also International, national, or regional and other "macro" caches which maintain copies of highly popular documents. These cache servers are often located at network gateways and backbone connections. These macro caches usually store copies of the documents stored at all the local or regional caches that are connected to it.
Why cache?
As the volume of World Wide Web traffic continues to grow, as much as 80 percent of the data becomes redundant. Why? The traffic consists of Web pages viewed by many people, repeatedly, over the same connection. Caching reduces delays caused by Internet bottlenecks and saves valuable bandwidth by retaining current copies of frequently requested material closer to the end-user. Caching delivers radical performance gains to the end-user and substantial cost savings to ISPs and corporations.
Caching is expected to be a key element of the infrastructure for the next generation of the Internet. There are campaigns online to promote the awareness and use of caches, e.g. Cache Now!. Collaborative Research, an independent Internet market research firm, estimates that the market for caching solutions will grow from $50 million in 1997 to more than $4 billion by 2002. This will be driven by both the growing need for the benefits that caching brings and the increasing maturity of the underlying technology.
If your organisation or ISP has a local cache you have to configure your browser to be able to use it. This is done by specifying a proxy server to connect to - instead of a direct connection to the Internet you connect through the proxy.
In Internet Explorer 6 this is done by selecting; Tools | Internet Options | Connections | Lan Settings | Reference : CacheNow ( http://vancouver-webpages.com/CacheNow/) 1999
What is a Proxy server ?
A proxy server is a server that acts as an intermediary between a network user and the Internet so that the network can ensure security, administrative control, and caching service. Proxies "represent" users by intercepting their Internet requests and managing them for users. A proxy server is part of the gateway server and firewall that separates the network from the Internet.
A proxy server receives a request for an Internet service (such as a Web page request) from a user. If it passes filtering requirements, the proxy server, assuming it is also a cache server, looks in its local cache of previously downloaded Web pages. If it finds the page, it returns it to the user without needing to forward the request to the Internet. If the page is not in the cache, the proxy server, acting as a client on behalf of the user, uses one of its own IP addresses to request the page from the server out on the Internet. When the page is returned, the proxy server relates it to the original request and forwards it on to the user.
To the user, the proxy server is invisible; all Internet requests and returned responses appear to be directly with the addressed Internet server. (The proxy is not quite invisible; its IP address has to be specified as a configuration option to the browser or other protocol program.)
The functions of proxy, firewall, and caching can be in separate server programs or combined in a single package. Different server programs can be in different computers. For example, a proxy server may in the same machine with a firewall server or it may be on a separate server and forward requests through the firewall. Microsoft offers a Proxy Server (http://www.microsoft.com/proxy) for its Windows NT system that also performs caching. Harvest (http://harvest.transarc.com) and Squid (http://squid.nlanr.net/Squid) are two popular freeware programs for UNIX servers that combine proxy and cache functions.
Switching a proxy on/off
One of the more annoying things when you carry a laptop between home and work is that you constantly have to turn the Browser Proxy on (for work) and off (for home).
To find out how to add a single click Proxy on/off extension to your Web Browser in windows, check out my blog entry
 References
References
- ↑ Firewall (computing). (2010, November 13). In Wikipedia, The Free Encyclopedia. Retrieved 09:55, November 14, 2010, from http://en.wikipedia.org/w/index.php?title=Firewall_(computing)&oldid=396490117
|
virtualMV | Superquick wiki guide | Please give me some feedback |
VirtualMV/Internet and Web/Gateway Servers. (2024). In WikiEducator/VirtualMV wiki. Retrieved November 21, 2024, from http:https://wikieducator.org/VirtualMV/Internet_and_Web/Gateway_Servers (zotero)
|