VirtualMV/Internet and Web/Email
| Internet and Web | ||
|---|---|---|
| Theory | Introduction | What is HTML? | Client Server ecosystem | Glossary | History and Future | How the Internet works | Types of Website | Markup Languages | Interactive Websites | | |
| Web Tools | Web Browsers | Search Engines (SEO Optimization) | World Wide Web (Hypertext and Page) | Cookies | Email | Discussion Forums | FTP | (SSH, IRC) | |
| Technologies | Connecting | Broadband | Mobile | Web Conferencing | Intranets, Extranets, Tunneling | Gateway Servers | | |
| Issues | Security | Legal (Privacy, Confidentiality, Integrity) | Copyright and Fairdealing | Accessibility | Culture and Netiquette | | |
| Web Site Development | Planning ( Types | For Mobile) | Development (Design Components | Graphic Design) | Programming | Hosting | Marketing and Promotion | Advertising | Business Intelligence | Monitoring and Maintenance (Performance Tuning) | |
| Web Site Management | Roles | Management | User Expectations | Content Management | Site Maintenance | Policies and Guidelines | Promotion | Risk Management | |
Overview
By the end of this page you will be able to give an explanation of the theory and usage of Internet tools including:
|
Evolution of a culture
Most of the traffic in the early days was messages sent between researchers. While many of the messages were notes about long distance networking, such as suggestions for improving the software and hardware of the network, they also included news, gossip and discussion about hobbies. It was not long before the invention of the mailing-list, in which an identical message could be sent automatically to large numbers of subscribers. One of the first really big mailing-lists was "SF- LOVERS," for science fiction fans.
Requests for comment (RFC)
Right from the beginning of the Net, the collaborative procedures for running and improving it began to evolve. People posted documents for discussion, these were known as Requests For Comment (RFCs) and anyone could comment on them.
After the period of comment a document would be finalised and no changes were permitted from then on, although an RFC could be superceeded by a new RFC which could contain parts from older ones, or build on them. RFCs are numbered sequentially, and there is an archive of every RFC ( http://www.rfc-editor.org/rfc/ ) from 1 to 2500 (and more). You can search the archive ( http://www.rfc-editor.org/rfc.html ).
No vendor "owns’ the Internet or the TCP/IP technology and there is no professional body responsible for the standards. So how does the system work? Since the beginning it has been a collaborative effort. TCP/IP has been developed over the years and as each development is suggested a message has gone out with a request for comments (RFC). Documentation of the protocols, standards and policies have and never will be available from a vendor. Instead, a group at AT&T (the American telephone company) have been given funds to maintain and distribute information. The Internet Network Information Centre (INTERNIC) handles administrative details. This documentation appears in a series of reports called Requests For Comment (RFCs) which anyone could comment on. After the period of comment a document would be finalised and no changes were permitted from then on, although an RFC could be superceeded by a new RFC which could contain parts from older ones, or build on them. They are numbered sequentially. They can be standards or proposals for new standards. If you ever feel like reading technical material you can.
On behalf of the Internet Society, the Information Sciences Institute (ISI) at the maintains a searchable index of all Requests for Comments from the Internet Engineering Task Force (IETF): http://www.rfc-editor.org/rfc.html
Internet fans can vote for their favorite RFC at this address!! There are now more than 2500 RFCs, they are all archived at: http://www.rfc-editor.org/rfc/
RFC 1 (1969): title page Network Working Group Steve Crocker Request for Comments: 1 UCLA 7 April 1969 Title: Host Software Author: Steve Crocker Installation: UCLA Date: 7 April 1969 Network Working Group Request for Comment: 1
Future of email
- Google wave (http://wave.google.com ) melds e-mail, instant messaging, online forums, and wikis into a grand messaging service. Due for release late 2009
History
Snail Mail
For traditional "snail" mail, you wrap your message in paper, seal it with spit, and give it to the government for two or three days. Then a government employee walks down your street and leaves it in a box on your front lawn!"
John O’Hara (1996) - Head of Telecoms Xtra believes the eMail security issue is overblown.
1971 - email invented
Ray Tomlinson gave society one of the greatest communication tools in history. He invented email back in 1971 -- essentially fostering global business communication and turning the Internet into a digital kitchen table for far-flung family members.
And the first email message .. "QWERTYUIOP"
(Who is Ray Tomlinson?, 2002) [1]
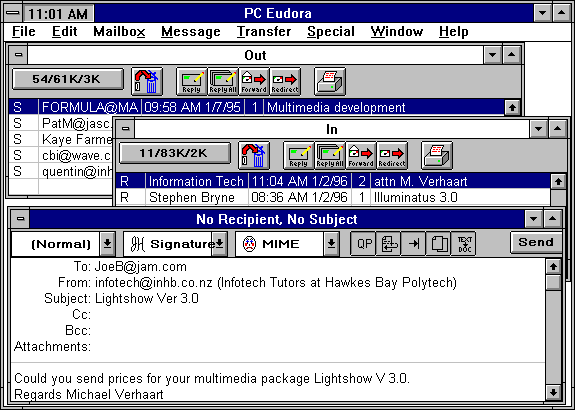
Eudora email client 1996
How email works
Email format
An Email address is made up of a username, the @ sign, then the domain name. Address format examples
- name@gmail.com,
- name@xtra.co.nz
- name@eit.ac.nz
Can be sent to anyone in the world as long as the address is correct!
How an email is sent, stored and retrieved
An email is composed on your computer, and "sent" to an outbox .
Once you are ready to send the mail (like taking it to a postbox), you initiate a "send and receive" command. This sends any mail in your outbox to your ISP (Internet Service Provider), and retrieves any mail currently stored with your ISP.
The ISP’s mail server then sends your mail out to other computers on the internet. Each computer reads the email address, then routes it to another computer (router) until it eventually reaches its destination.
It is then stored in an electronic mailbox, until the recipient logs in and checks their mailbox. If you have an ISP (Internet Service Provider) the message is held on their server until the next time you use the service, when you are advised ’you have new mail’.
Working with email
Once an email message has been read is can be
- Replied to,
- Forwarded to another email address,
- Filed in a folder or
- Deleted.
What's the number of unread emails—right now, at this moment, without changing anything—in your inbox? That would be 3,487 in the case of Jen; 1 in the case of Rebecca. ...What Your Email Inbox Count Says About You (Greefield, 2012)[2]
Tips & Tricks
Software
eMail client
Software that allows you to read, write (compose), reply, forward, file and delete messages. Most also allow you to store email addresses in an address book, conduct a text searches, add a signature files, and automatically send incoming email into specified folders based on who the message is from (message filtering)
Web mail
One trend is the use of the web browser to work with email.
- Advantages include;
- Don’t need an ISP account.
- Free
- Commonly included with existing email systems. (e.g. xtra )
- Log into a Web site and access your email
- Very useful for travellers (though watch how you use it in public kiosks as others may browse your email with forward and back buttons!)
- Disadvantages include;
- Due to server congestion it often takes ages to log on and access mail
- Has adverts
- Most now adding opt-in newsgroups where you select interest areas.
- Examples
- hotmail.com, gmail.com and most private email systems have a web browser interface to access the email from anywhere.
Webmail accounts
- Temporary 10 Minute Email ( http://10minutemail.com )
- If you ever need a temporary email address, maybe for a coupon code for a one-time purchase (Then they fill your inbox with unwanted offers and other advertising). Or, maybe just to test your own email setup is working ok. With 10 Minute Mail you get a temporary email address that lasts for 10 minutes or you can keep adding another 10 minutes if the email you are expecting is late.
- When you arrive at the site you’ll be automatically loaded into your mailbox. There’s no need to register or anything like that. Instead, copy the e-mail address they’ve provided for you and use it. If you need to check an e-mail for whatever you signed up for it will come directly to the page you’re on, in the message section near the bottom of the page.
Issues
Security
E-mail is not private and can be read by system administrators
- at your organisation’s mail server
- at any of the routers along the way
- at the destination mail server
Think of e-mail as you would a post card. Avoid including any confidential information unless you encrypt it. With billions of emails sent and received it’s unlikely that anyone will ever look at your email.
In 1998 careless comments about the performance of a rival company in email by staff of Norwich Union in the UK cost them 450,00 pounds ($NZ1.1million) in damages.
Reference : Palmer, G. (1998, Apr) You`re Fired!. , NZ PC World 104. ISSN 01114 7285 pp 34-38
Privacy
Strangely few people would even think of using their work phone to natter to friends in Sweden for an hour, but they will happily spend that time composing an email message." - Geoff Palmer (1998)
- Email is not private. It’s more like a postcard - and a postcard that may have been photocopied by everyone who handled it.
Deleting email only removes it from your PC, not from any of the dozens of copies made on its path to you. Workplace email is company property. It may be monitored by your employer and what you say on it is both yours and your employers responsibility. People have been sacked for what they have sent. The smoking gun
- In a legal sense "to publish" mearly means "to make public". Airing your views in the tea-room is considered publishing as is sending an email. Hence, either can be used in a defamation case. If you tell a racist joke (or eMail it) you can be prosecuted under the Human Rights legislation. If you bad mouth someone, you can be sued for defamation. As one US lawyer described it "Email is the smoking gun". Don’t assume that an email sent to one person will remain with that person. Forwarding an email to many others is easy, and guess who’s name is on the top!
Anatomy
Header
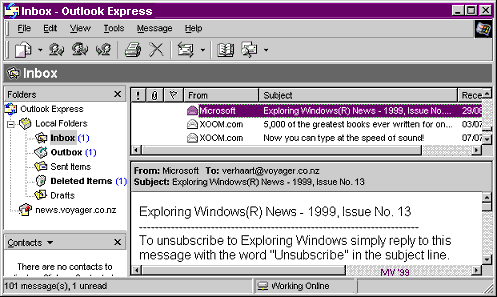
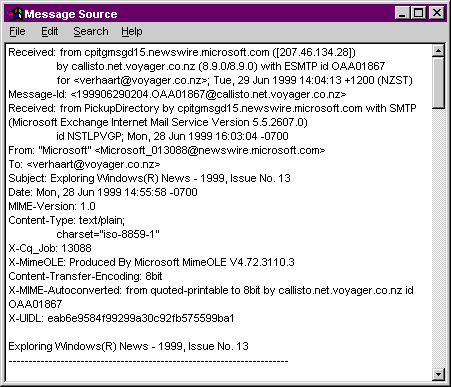
Emails are similar to letters, with two main parts. The header contains your name and address, the name and address of the person of all the recipients, the date of the message and a subject - what the message is about. When you receive an e-mail, the header tells you where it came from, how it was sent, and when. It’s sort of like an electronic postmark. Normally only part of the header is displayed in the message, e.g.
From: support@xdrive.com Date: Wednesday, 2 Augudst 2000 21:07 To: verhaart@xtra.co.nz Subject: Congratulations
But the whole header can be accessed too, as shown.
Body
Text of the message. Format:
- Until recently, e-mail on the Internet was only composed of plain text.
- With the advent of MIME, ( Multipurpose Internet Mail Extension), and other encoding schemes, (eg. UUencode), messages, formatted documents, photos, sound files, and video files can be electronically sent.
- Requires the recipient of the email to have the decoder.
- Email can also be sent in HTML. This means that the message can have all the features available to a web page.
Mailing Lists
Types
One of the biggest advantages of email over normal mail is the ability to send an email to multiple recipients for no extra cost. These are called mailing lists and there are two main types. A distribution list is where one person stores a list of email addresses in their email client software and gives it a name - when they want to send an email to all the addresses on that list they just enter the name of the list into the To: field. A distribution list to send messages to all students or group leaders in a class is typical.
The second type of mailing list are discussion lists where groups of people on the Internet world wide get together to discuss a particular subject (to find a mailing list on a subject that interests you try a search at http://liszt.com/ where over 90,000 lists are registered). Discussion lists are often called listservs after one of the most popular pieces of software used to run them (the other popular list management software is called majordomo). Typically anyone can send an email message to a listserv and it will be forwarded or bounced to all the subscribers of that list.
A third type of list is a marketing list, where you receive information about certain products (e.g. Xoom.com - where up to 2 emails a week is common). It can be a problem to keep your name off these lists, or even unsubscribing. If you publish anything on the Internet (including a post to a newsgroup), your email may be gathered. A variation of the marketing list appeared in 2000, the Opt-In email. Customers elect to receive email and self-report personal interests. Forrester Research (Mar 1999) suggest opt-in email have an 18% click through rate compared to banner ads of 0.65%. In 2000, advertisers typically paid $0.50 per name, roughly half the price of a postal direct mail campaign. Opt-In NZ ( http://www.optin.co.nz ).
Subscribing
Lists may be open (anyone can send a message to them) or closed (only subscribers can send messages). They may also be moderated (all messages sent to them are checked for suitability by an editor before being sent to subscribers). They may also be private, where you have to ask to join or public, where anyone can join. Mailing lists often have informal rules of conduct so you are advised to simply read the mail that is distributed for some time (this is called lurking) before joining in the discussions by posting a message. Lurking will also allow you to check that that mailing list is the right one for you.
To subscribe to a list you simply send an email to a certain address. (Often you put no message in the SUBJECT field and in the body of the message you type subscribe list-name). Once you have subscribed you will be sent a welcome message which will also give instructions for unsubscribing - it is vital that you save this message, or you may not be able to remove yourself from the list. Some mailing lists can send out hundreds of messages a day, so remember to unsubscribe when you are on holiday or you may return to find your mailbox overflowing!
Netiquette
Netiquette (Internet Ettiquette), is the set of informal shared rules that govern people’s behaviour on-line. If a user is irresponsible or discourteous to others or abuse the resources that allow them and others to share information and communicate, then that user runs the risk of incurring the wrath of the Internet community. Netizens will, individually or collectively, educate, inform and sometimes even ostracize the user. In the worst cases netizens may contact the user’s Network Administrator and inform them of the abuses, and often the user may lose their network account. Generally, if you use common sense, and apologise if you make a mistake, then you will travel the Information superhighway safely.
http://cleo.murdoch.edu.au/help/activities/netiquette.html
General rules
- Mind your manners and consider other people’s feelings at all times. Never say anything over the wires that you would not say to a person’s face.
- Think before your write. Don’t say something you will be sorry for later. These documents could be permanent. Treat every post as though you were writing to your mother! Remember other people may read the email.
- Be wise in your choice of words. Verbal opinions expressed on paper lack the nuances of spoken language and body language and are often taken the wrong way by the recipient. You can indicate emotion using "emoticons" such as the smiley :-) or the ironic smiley ;-) . Refer to Smileys which contains many more emoticons, however you should be aware that few emoticons apart from the two above are in general usage.
- Don’t talk about anybody in a post and certainly don’t betray a confidence. Don’t forward someone’s mail without their permission.
- Don’t send lines longer than 70 characters. Although this is changing many people still use DOS based systems and many gateways truncate extra characters.
- DON’T SEND A MESSAGE IN ALL CAPS IT’S HARD TO READ.
- Use normal capitalisation. All lower case can be insulting to some people.
- You can use CAPS for emphasis.When e-mail was text based we used the underscore key at the beginning and end of a phrase to indicate that it is a source or to indicate italics. e.g. "Jerry Mander’s _In Absence of the Sacred_ is a book on questions we should have asked about technology".
- With email it is not as important to use correct spelling and grammer as it is for a letter, but you should try to keep your spelling and grammar as correct as possible as this is a source of annoyance to some people.
- Avoid Vague Subjects
Smileys/Emoticons
:-) Your Basic Smiley
:-o Wow!
:-| Grim
:=| Baboon
:-v Speaking
:-V Shout
:-w Speak with forked tongue
:-r Sticking tongue out
:-* Oops!
:-T Keeping a straight face
:-D Said with a smile
:-x Kiss kiss
:-[ Pouting
:-X A big wet kiss!
8-| Eyes wide with surprise
\-{ "Good Grief!"
8-} "wow, maaan"
:-, "Hmmmm"
:^D "Great! I like it!"
*<:-) User is wearing a Santa Claus Hat
:-c Real unhappy
:-C Just totally unbelieving
:-B Drooling
:-, Smirk
:-|| Anger
:-) Smiling
:-( Frowning
‘-) Wink
;-) Sardonic Incredulity
%-<I> Drunk with laughter
:-" Pursing lips
:-# My lips are sealed
:-Y A quiet aside
&-| Tearful
:-} "This wine tashted pretty good"
8-O "Omigod!!"
:-P Tongue hanging outReferences
- : (11 April 2003) Acronyms, Emoticons & Smilies Page. Retrieved May 15, 2003, from http://www.muller-godschalk.com/emoticon.html
- netlingo (n.d.), Smileys and Emoticons Retrieved August 3, 2006 from http://www.netlingo.com/smiley.cfm
Japanese Smileys
Japanese smileys don’ require you to turn your head.
Examples
^-^, standard phappy smiley. The longer the mouth the happier -_-, disgruntled (---^_^---), Smiley hug. The longer the arms the bigger the hug. *_*, Shocked, startled !_!, shocked, startled ^_~, mischevious wink ;_;, crying ^_^/~, waving hanky n_n, really happy ?_?, clueless ^_^/, Yippie. =^_^=, cat
Hanmeier, J (n.d.) Japanese Smileys: An otaku’s unofficial guide. Retrieved 2007, April 23 from http://www.deadlybrain.org/writings/japanesesmileys.php
Abuse
Mail bombing
It can be a problem to keep your e-mail address off certain mailing lists - those kept by Internet marketing organisations. If you publish your email address on the WWW or Usenet it can be gathered, and you may find yourself receiving email asking if you want to buy for example, some computer equipment or a Russian bride! Mailinator ( http://www.mailinator.com ) A service introduced in 2003 that allows you to enter a ficticious email address. This address is automatically created and any subsequent emails sent to this account. Or to quote "Have you ever needed an email .. NOW? Have you ever gone to a website that asks for your email for no reason (other than they are going to sell your email address to the highest bidder so you get spammed for ever (and ever (and ever)))? Get your email sent here, THEN come check mailinator. Your mail will be waiting."
You can also be mail-bombed, which is when a person or a group sends so many copies of a message to a single mailbox with the explicit intention of overflowing the recipient’s mailbox. Mailbombers can also subscribe someone to numerous e-mail lists without their knowledge, once again causing the mailbox to overflow. We must therefore be careful not to offend whilst using e-mail. Email etiquette is covered separately.
Flaming
Flaming is sending an abusive or angry message to someone, and should be avoided. "Flames" are often sent in reply to a mistake that someone has made - instead you should politely point out the mistake and ask them to modify their behaviour. You should never flame anyone who simply disagrees with you - they are intitled to their opinion, no matter how wrong you think it is. It is better to politely reason with them. Do not antagonise people. There is more to do in life than insult people. Above all, keep calm: you may have misinterpreted the implied criticism or missed the ironic humour in a message; don’t send a reply while you are still hot under the collar.Wait a while until you cool down before answering.
If you must argue with someone, do it via private email, never on a disscussion group (usenet). No-one else wants to read your argument. A fight occurring on-line between two or more people is called a "flame war". These replies and counter-replies clutter up the discussion and annoy the other group members. In cases like this, both parties are wrong and acting quite childishly because they are inflicting their temper tantrums on everyone that uses that group.
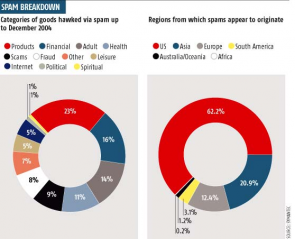
Spamming
Spamming is the practice of sending the same post (usually adverts) to a great number of newsgroups on the Net, or sending unsolicited mail (again usually adverts) to millions of email addresses at once. Internet marketing organisations get their lists of email addresses from robots that trawl the WWW and newsgroups gathering valid email addresses. Spamming annoys many people, and there are campaigns on-line to stop the practice.
An example of spamming is the couple called Lawrence Canter and Martha Siegel who became, for a time, the most hated couple in cyberspace. They wrote a program, which put a little advertisement in every bulletin board on the Internet. At that time there were approximately 5,500. It was seen by millions of Internet users, not just once but over and over again. Net users were subject to `thousands of pieces of Junk mail’. The incident became known as the `green card’ case because the couple had advertised help to people wanting green card `permanent entry’ into the United States. Angry network users flamed the couple so much that their computer crashed. As a result their network provider finally pulled the plug on them.
Bulk e-mail refers to sending e-mail to large numbers of recipients. Usually to people who have requested the service. It’s different from spamming because it’s requested. Reference : Harris, D. (1999, May/Jun ) Law change only cure for spam, . , Network world No. 31, p 8.
Most ISPs automatically delete mail from recognised spammers (From Nov 2003 - Xtra added a spam filter to xtramail)
Spam can bring your site to its knees or take enormous amounts of administration time to clean up. Spam can be generated by humans and machines (bots). Bad behaviour is an example of spam management extensions for several applications (such as Mediawiki)
2011: Study sees way to win spam fight
University of California, San Diego (UCSD) researchers completed a study aimed at finding a choke point that could reduce the flow of spam emails. The researchers tried to receive as much spam as possible for three months and then they bought items from the Web sites advertised in the messages. The researchers, led by UCSD professor Stefan Savage, found that 95 percent of credit card transactions for spam-advertised drugs and herbal remedies were handled by three main financial companies, one of which was in Azerbaijan, one in Denmark, and one in the West Indies. Savage says the study indicates that "you'd cut off the money that supports the entire spam enterprise" if those companies stopped authorizing online credit card payments to the Web sites. The researchers found that spam systems rely on just a few banks and even fewer credit card processors, which is a glaring weakness that regulators and law enforcement agencies can exploit. "The defenders can, in principle, identify which banks the scammers are using far faster than they can get new banks, and for basically zero cost," Savage says. (Markoff, 2011, May 19) [3]
2003: Survey Says Spam Wastes Your Time
Tired of spam? You’re not alone: 49% of Americans spend more than 40 minutes per week deleting unwanted email, with 14% reporting they spend as much as three and a half hours a week -- or 7.5 days per year -- on this task, a "McAfee Americans and Spam Survey" conducted in 2003 reveals.
Reference : Survey Says Spam Wastes Your Time (2003). Retrieved March 08, 2003, from http://us.mcafee.com/root/campaign.asp?cid=8187
2009: Survey, How big is Email?
A Survey done by The Radicati Group projects there to be 1.4 billion email users (2009)and an estimated 1.9 billion in 2013. Radicati group also puts email trafic at 247 billion messages per day (2009). (The Radicati Group Inc., 2009)[4]
-Stickypotato 12:54, 31 August 2010 (UTC)
2003, Sept. 23: California Gov. Gray Davis Signs Bill to Ban Online Spam
California Gov. Gray Davis signed Sen. Kevin Murray’s (D-Calif.) anti-spam legislation into law Sept. 23, thus criminalizing the sending of unsolicited commercial email to Californians and allowing state Attorney General Bill Lockyer, ISPs, and individual residents to file civil suits against spammers and their advertisers. Spam marketers and advertisers exempt from the law, which imposes a $1,000 fine for every unsolicited message, are those who get specific requests from recipients to send them email or who have previous business relationships with recipients. In addition, a fine of up to $1 million can be charged against bulk emailers who conduct blitz campaigns, in which hundreds of thousands, sometimes millions, of unsolicited messages are sent out on a daily basis. (Ingram, 2003)[5]
Project Honeypot aims to trap spammers
"Jeremy Jaynes was found guilty last November by a state court in Leesburg, Virginia, of sending more than 10 million unsolicited emails a day. He was hawking pornography, work-at-home schemes and stock-picking software. The spams are estimated to have earned him around $750,000 a month. He is now on $1 million bail, forbidden from using the internet and will be sentenced this month. The jury has recommended he gets a nine-year jail term."
Unspam (2005). Project honey pot. Retrieved February 4, 2005 from http://www.projecthoneypot.org/
Boston, C (2004) Project Honeypot aims to trap spammers. New Scientist, Reed Business Information Ltd. Issue 2485, p26. Retrieved February 4, 2005 from http://www.newscientist.com/channel/info-tech/mg18524856.900
Purchasing email lists
Email Marketing !
We offer you e-mail addresses databases for advertisement mailing; we sell databases also carry out mailing and hosting for the advertising projects.
Products
World Email Lists . Their validity and originality are verified. please go to our web: http://202.98.223.74/soft/html/wd/wd3.htm There are some sample download.
Country or area total emails and price
America 175 Million Email Address $220 US Europe 156 Million Email Address $250 US Asia 168 Million Email Address $150 US China(PRC) 80 Million Email Address $200 US HongKong 3.25 Million Email Address $200 US TaiWan 2.25 Million Email Address $200 US Japan 27 Million Email Address $200 US Australia 6 Million Email Address $150 US Canda 10 Million Email Address $150 US Russia 38 Million Email Address $120 US England 3.2 Million Email Address $200 US German 20 Million Email Address $200 US France 38 Million Email Address $150 US India 12 Million Email Address $120 US CENTRAL & SOUTH AMERICAN AREA 40 Million Email Address $220 US MIDDLE EAST & AFRICA 45 million Email Address $220 US SOUTH EAST AREA 32 million Email Address $220 US
Examples
Software installer scams
From: Abuse Team Robot [kbosl@csplc.com] Subject: Trojan Detected! Dear Customer, Our robot has detected an abnormal activity from your IP adress on sending e-mails. Probably it is connected with the last epidemic of a worm which does not have official patches at the moment. We recommend you to install this patch to remove worm files and stop email sending, otherwise your account will be blocked. Abuse Team Robot
Online qualifications
From: "Michelle" To: Sent: Thursday, 25 January, 2001 7:32 PM Subject: Confidentiality Assured ! UNIVERSITY DIPLOMAS Obtain a prosperous future, money earning power, and the admiration of all. Diplomas from prestigious non-accredited universities based on your present knowledge and life experience. No required tests, classes, books, or interviews. Bachelors, masters, MBA, and doctorate (PhD) diplomas available in the field of your choice. No one is turned down. Confidentiality assured. CALL NOW to receive your diploma within days!!! 1-212-???-???? Call 24 hours a day, 7 days a week, including Sundays and holidays.
Nigerian Scam
From: "donald fxxxxx" To: Sent: Monday, 15 January, 2001 11:28 PM Subject: private business proposal. Private Business Proposal. Dr. Donald Fxxxxx 16 Kingsway Road Ikoyi, Lagos, Nigeria. Tel/Fax: 234-1-??????? 16th January, 2001. Attention: Managing Director/ C.E.O. Sir, Request for Urgent Business Relationship. First I must solicit your confidence in this transaction. This is by virtue of its nature as being utterly confidential and top secret. We shall be counting on your ability and reliability to prosecute a transaction of great magnitude involving a pending business transaction requiring maximum confidence. We are top officials of the Federal Government Contract Review Panel who are interested in importation of goods into our country with funds which are presently trapped in Nigeria. In order to commence this business we solicit your assistance to enable us RECIEVE the said trapped funds ABROAD. The source of this fund is as follows : During the regime of our late head of state, Gen. Sani Abacha, the government officials set up companies and awarded themselves contracts which were grossly over-invoiced in various Ministries. The NEW CIVILIAN Government set up a Contract Review Panel (C.R.P) and we have identified a lot of inflated contract funds which are presently floating in the Central Bank of Nigeria (C.B.N). However, due to our position as civil servants and members of this panel, we cannot acquire this money in our names. I have therefore, been delegated as a matter of trust by my colleagues of the panel to look for an Overseas partner INTO whose ACCOUNT the sum of US$31,000,000.00 (Thirty one Million United States Dollars) WILL BE PAID BY TELEGRAPHIC TRANSFER. Hence we are writing you this letter. We have agreed to share the money thus: 70% for us (the officials), 20% for the FOREIGN PARTNER (you), 10% to be used in settling taxation and all local and foreign expenses. It is from this 70% that we wish to commence the importation business. Please note that this transaction is 100% safe and we hope that the funds arrive your account in latest ten (10) banking days from the date of reciept of the following information by TEL/FAX: 234-1-???????: A suitable name and bank account into which the funds can be paid. The above information will enable us write letters of claim and job description respectively. This way we will use your company’s name to apply for payments and re-award the contract in your company name. We are looking forward to doing business with you and solicit your confidentiality in this transaction. Please acknowledge receipt of this email using the above Tel/Fax number. I will bring you into the complete picture of this pending project when I have heard from you. Yours Faithfully, Dr. Donald Fxxxxx.
 References
References
- ↑ Who is Ray Tomlinson? (2002). Retrieved July 23, 2002, from http://www.rit.edu/~kac4253/imm/project1/project1.html
- ↑ Greefield, R. (2012) What Your Email Inbox Count Says About You. Retrieved from http://www.theatlanticwire.com/technology/2012/12/zero-dark-inbox/59863/
- ↑ Markoff, J. (2011, May 19) Study Sees Way to Win Spam Fight. Retrieved from http://www.nytimes.com/2011/05/20/technology/20spam.html?_r=1
- ↑ The Radicati Group Inc. (2009) Releases “Email Statistics Report, 2009-2013” retrieved 18 August 2010. http://www.radicati.com/?p=3237
- ↑ Ingram, C. (2003,Sep 24) California Bans Spam, Sets Fines. Retrieved September 25, 2003, from http://www.latimes.com/business/la-me-privacy24sep24,1,7231912.story?coll=la-home-leftrail
|
virtualMV | Superquick wiki guide | Please give me some feedback |
VirtualMV/Internet and Web/Email. (2025). In WikiEducator/VirtualMV wiki. Retrieved February 18, 2025, from http:https://wikieducator.org/VirtualMV/Internet_and_Web/Email (zotero)
|