4. Crime and Cybersecurity
From WikiEducator
- Crime - an unlawful act punishable by a state or other authority.
- The term "crime" does not, in modern criminal law, have any simple and universally accepted definition. One proposed definition is that a crime or offence (or criminal offence) is an act harmful not only to some individual but also to a community, society or the state ("a public wrong"). Such acts are forbidden and punishable by law
With the assistance of technology, there are many new ways to commit crimes. However, with cybersecurity, there are also new ways to detect and prevent crime, as well. We look at both sides - good and evil.
Learning outcomes
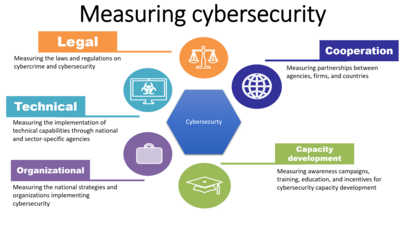
- understand issues associated with computer crime and cybersecurity
- find web resources appropriate to the topic
- facilitate student discussion
- learn to work collaboratively online
Keywords
- hacking, virus, identity theft, fraud, scams, civil liberties, law enforcement, punishment, prevention, cybersecurity
Study notes
- What are some new forms of criminal behavior that did not exist before the internet? What crimes are easier with the aid of computers and technology?
- Worms and virus - have you been attacked or infected? What was the "cost" to you in time, effort or money? Should the creators be punished for spreading these? What is suitable punishment?
- Is any hacking harmless?
- Should the age of the hacker be taken into consideration when judging these crimes? Why or why not?
- Who is ultimately responsible for the security of computer assets? To what extent can the owner expect that others will abide by the laws and not harm the information?
- What are some of the technologies that improve security?
- Is spam really a kind of theft? How big a problem is spam? What steps do you take to avoid spam?
- Do you understand identity theft? What steps do you take to prevent your identity being stolen? Are you personally concerned about having your identity stolen?
Contents
Assignments
- Before you start the reading and the assignments, take a few minutes to think about what you already know about the topic - Crime & Cybersecurity. What don't you know? What questions do you have? Write a sentence or two about this in the I have questions... discussion.
- Read the Study notes for an overview for the topics that will be covered.
- Read the article Crime on the Internet. This is an older article. Some more recent examples are not included.
- Read a few items in the current issue of the Risks Forum http://catless.ncl.ac.uk/Risks and post a brief 2-3 sentence summary of one item to Risks Forum discussion. Include a link to the item you select.
AND Review the posts of 2 other students and post a personal note (2-3 sentences) about your experience or understanding of the risk and how it related to society to each of these.
- Search the web for sites that talk about crime & cybersecurity. Find a site that you think is particularly interesting. Write 2-3 sentences about the social issues discussed. Post a link to the web site and description to the Crime & Cybersecurity discussion. To encourage more discussion, include a question in your posting. Is there another side to the story? Is there information that you need to understand the site you found? Be sure to ask a question that will get the discussion going about the topic.
Follow links provided by other students and read through the page or articles. Reply to 2-3 other postings. Respond to the question. End your reply with your own questions. You are not limited to the number of posts - the objective is to get some discussion going here.
- Do you think you know an email scam when you see one? Take the Phishing IQ quiz and see if you can tell the real corporate emails to customers from the phishing scams. I missed 1 scam but I would have ignored two real requests from companies I do business with.
https://www.sonicwall.com/phishing-iq-test/
- Trends in Scams and Fraud. It seem that there is always a new scheme to rip-off your money or your personal information. What are some of the latest schemes we need to be aware of? Have you seen any of these - email, social media? Find a description of a scam and post the link and a brief summary of the potential danger to Scam Trends discussion. Review several others. This is for your own protection.
- Now what? - If you or someone you know has had their identity stolen or their computer hacked, what should they do? Find a resources with advice to help people recover from this situation. Post your link and a brief description of who could benefit from this resource to Hacked - now what? discussion.
- Blockchain - with all the cyber crimes being devised and committed, people are looking for new ways to prevent them and ensure that exchanges of information and money are secure. Blockchain is one such solution. It is the underlying technology behind cryptocurrency and NFTs. Blockchain technology is also use to authenticate credentials and other important information. Find a resource that talks about blockchain and related technologies. Post the link to your selected resource and a brief description to the Blockchain technologies discussion. Review 2 others.
- There ought to be a law - With all the new technologies, there are plenty of opportunities for criminals to cause problems for users. This presents problems of law makers and law enforcement around the world. What are some laws that are being considered? What problems are there with making laws against technology crimes? What are some of the technology crimes that there should be laws against? Find a resource that addresses the issue of enacting and enforcing laws against technology crimes. Post a link to your resource and brief summary of the problems associated with the crime and the laws to the There ought to be a law discussion. Review 2 others.
- Relationships. Has technology and the internet change interpersonal relationships? What defines a relationship? What does the research say about the nature of relationships today? Are there predictions about the future of relationships? Find a resource that addresses these issues. What do you think about the information provided in the resource you selected? Post a link and a comment to the Relationships & Technology discussion. Eeview 2-3 others. Add comments or questions if you have them - optional.
- As new web-based services are provided and people share information, social media has evolved. Here are 50 of the biggest social media questions answered. Select 2 answers that you didn't know before. Why is this information important? Post your new information and a description of your own social media experience in the discussion Social Media Questions.
- Learning Literacies - Solve it - There are many tools available on the web to help with problem solving skills development and practice. Critical Thinking, Problem Solving and Decision Making are the primary focus of the articles provided. Review articles in the Solve it media selections and find an online example of applying this skill. Post a link and a brief summary to the Learning Literacies - Solve it discussion. Review 2 others.
- Read the Collaboration guidelines.
- Project Groups Discussions - The groups were randomly assigned by Canvas. This is as good a way to form groups as any. Learning to work in online groups and practicing these skills are important preparation for careers in any field. If you already have experience working in groups online, please post 1-2 sentences about your experience. If you have not worked in a group online, what questions do you have? Post your reply to your Project Groups Discussions. If you can, respond to questions from others.
Note: There will be several group activities throughout the course. You will have a partial score until you have completed all the group discussion tasks in the course. Points are awarded for participation throughout the course so you will see your score increase after each task.
- Reflection - How long did you work on the assignments for this week? Is this about the same as it usually takes to complete the work each week? Is the pace of work for this class about right? What would you like changed in the course? What would help you learn more about Computers and Society? Please comment. This should be 3-4 sentences submitted as I think... assignment.
CRIME
- Popular Android TV boxes sold on Amazon are laced with malware | TechCrunch
- Milisic said the malware’s default payload is a clickbot, essentially code that generates ad money by surreptitiously tapping on ads in the background. After the affected Android TV boxes are pow...
- First man wrongfully arrested because of facial recognition testifies as California weighs new bills | California | The Guardian
- In 2020, Robert Williams was arrested for allegedly stealing thousands of dollars of watches. Detroit police had matched grainy surveillance footage of the crime to Williams’ driver’s license p...
- How can I check if my email account has been hacked?
- "Scams are rising, and more people are falling for phishing attacks and email hacks than ever. Tap or click here to see how COVID-19 scams have become rampant.Just think about how many times a...
- NetWalker ransomware affiliate sentenced to 20 years in prison | TechCrunch
- Authorities in the U.S. and Belgium also seized the dark web site used by NetWalker to publish data stolen from victims.In March, Vachon-Desjardins was extradited to the U.S. to face charges of con...
CYBERSECURITY
- Cost of a data breach 2022 | IBM
- data breach in the US costs over twice the global averageFor the 12th year in a row, the United States holds the title for the highest cost of a data breach, USD 5.09 million more than the global a...
- SANS NewsBites - Cyber Security News
- NewsBites - Cyber Security NewsSANS NewsBites is a semiweekly executive summary of the most important cyber security news articles published recently. Each news item is annotated with important con...
- Business email compromise attacks going mobile via SMS and social media apps | SC Media
- "BECs remain one of the biggest cybersecurity threats today. The FBI has reported that losses from BECs have surpassed $43 billion globally and as time goes by, scammers are becoming more cunn...
- Cybersecurity - Florida SBDC Network
- Cyber-attacks against small businesses are on the rise. Small businesses are, unfortunately, attractive targets because they have information cybercriminals want and often don’t have the expertis...
SOLVE IT
- 11 Active Listening Skills To Practice (With Examples) | Indeed.com
- One of the most critical skills in effective communication is active listening. Developing this soft skill will help you build and maintain relationships,solve problems, improve processes and retai...
- If you really want to reach your full potential, start saying “yes” to these 10 things
- For many of us, reaching our full potential seems like an impossible task. We’re stuck in our 9 to 5 jobs and don’t even know where to start.On the other side, there are people who have succeed...
- Steve Jobs Said Your Overall Success May Be Tied to This Powerful Thinking Habit | Inc.com
- Exercise "clean thinking"Before embarking on a new project or strategy, it's crucial to strip away the unnecessary complexities and, as Jobs stated, "get your thinking clean.&quo...
- 2013.09 1323 . 2015.6 2056 . 2016.6 3198 . 2018.5 5756 . 2020.12 12210 . 2021.12 12829