File Management and Protection/Common Threats/Securing your system
| File Management and Protection | |
|---|---|
| Common Threats | Introduction | Identifying common threats | Ensuring integrity | Securing your system | Key points | Assessment |
Securing your system
Measures are applied to secure your system against unauthorised access.
| Threat | How to prevent it |
|---|---|
| Unauthorised access leading to data corruption or deletion of your system and data |
Install a firewall and configure it so that an alarm automatically alerts you to a system attack Use logins and passwords on systems to activate intruder detection software to lock user out Restrictions on drives, and/or files eg password protect and/or folders to protect sensitive data Lock computer rooms, security personnel, swipe cards (limiting physical access), use video surveillance |
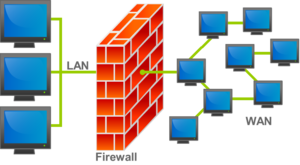
What is a firewall?
A barrier between the internet and your computer positioned at the point of entry/exit to your PC or system (Ports).
How do you set it up?
Configure your firewall so that it automatically alerts you if something is trying illegally to enter your computer system.