Internet & Web development (2)/Course materials/Web Site Issues/Security
| Internet & Web development (2) | ||
|---|---|---|
| Web Site Issues | Security ( Managing ) | Legal ( Privacy | Confidentiality | Integrity | Copyright and Fair Dealing | Contracts) | Accessibility ( Managing ) | Culture and Netiquette | |
Security issues and the Internet
There are many risks that you face when connecting to the internet. This page investigates some of the risks and looks at ways you can minimise these risks
Risks when connecting to the Internet
|
Resources
- Data security toolkit Sophos (n,d,)[1]
- Free tools to help secure your data, resources to explain security threats and security tips to share and help others
Security Threat Timeline
- 2014/05/22 - [http://www.nzherald.co.nz/business/news/article.cfm?c_id=3&objectid=11259488 eBay hacked, massive data theft suspected (2014)[2]
| Details |
|---|
|
An eBay email from Kari Ramirez said the database was compromised between late February and early March and "included eBay customers' name, encrypted password, email address, physical address, phone number and date of birth", but "did not contain financial information or other confidential personal information" or affect data from PayPal. "However, we believe there may be a large number of accounts involved and we are asking all eBay users to change their passwords." Potentially affecting eBay's 128 million active users globally, the attack could be one of the largest affecting a retailer, and comes just months after eBay disclosed a breach which could affect more than 100 million. The company said it detected "compromised employee log-in credentials" about two weeks ago and began an investigation."Cyberattackers compromised a small number of employee log-in credentials, allowing unauthorised access to eBay's corporate network". |
Cyberattacks
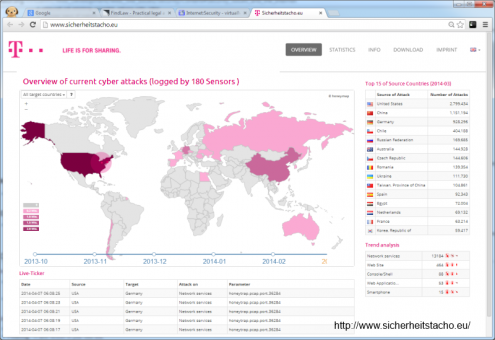
- 2013, March Overview of current cyber attacks (logged by 97 Sensors )
- Deutsche Telekom, a German telecommunications company, has developed a website that allows users to monitor cyberattacks as they http://www.sicherheitstacho.eu/ (loosely translated as "security tachometer") displays events as they happen, giving the time of the attack, country of origin and the intended target. (Honorof, 2013)[3]
Common threats that need to be addressed by web programmers
In a presentation Jackson (2009) [4] identified two types of security:
- Content Security (what)
- like customs at an airport. Controls what is permitted to enter or leave
- Firewall security (who)
- like immigration at an airport. Controls who is permitted to enter or leave
Jackson (2009) [4] identified the following threats that need to be considered by web programmers (The presentation can be downloaded from 2009JacksonKirk-WebSecurityNapier.pdf )
- User input - Don't trust user input. E.g. can add JavaScript into a comment box.
- Phishing - A fake version of your web site
- XSS – Cross-site scripting
- CDRF - Cross domain request forgery (Posting a form from one website to another)
- Click-jacking. Example program at Guya.net (2009) [5]
Others
- Spam: Can bring your site to its knees or take enormous amounts of administration time to clean up. Spam can be generated by humans and machines (bots). Bad behaviour is an example of spam management extensions for several applications (such as Mediawiki)
- Acitivity: how would you work out if this email was spam?
http://vimeo.com/81556880 You are receiving this communication because you have been identified as an Expert in your area of activity. We invite you to join the New Zealand Strategic Team. If you are a Dreamer who loves, a Lover who dreams, please do send us your one-paragraph biography to newzealand@dreamersland.us. 2,675 Expert Dreamers from 196 countries and territories have already joined the best team designed to serve the long-term public interest of society. -- JPMONFORT THE OFFICE OF JP MONFORT | Welcomes Dreamers to the Future | www ExpertDreamers info
In 2009 Kirk was a programmer with Xero (NZ online accounting software) and you can read more security tips (especially related to ASP programming on his blog (Jackson, 2010)[6].
Virus
Commonly attack your system via email attachments (macro virus, exe programs). There are many antivirus programs available including:
- Nortons, McAfee, Nod32
- Two well known - and free anti-virus programs are
- AVG ( http://www.avg.com )
- AntiVir ( http://www.antivir.com )
2012, Flame virus
Whoever is controlling the two-year-old, but only recently discovered, Flame virus has ordered it to self-destruct and erase all traces of itself to impede the forensic analysis of its code. On 6 June, Symantec reported that a self-immolation module has tried to locate every Flame file that has infected computers. The suicide module removes the files and then overwrites the disks with random characters in an attempt to leave no traces of the infection behind.
- IEEE Spectrum
- Heyes, J.D., (2012, June 12) Flame virus, most sophisticated malicious code ever seen, was developed by U.S. government
2003, Aug: Millennium malware month
SoBig(Sobig (computer worm), 2010[7]), W32/Blaster (Blaster (computer worm),2010[8]); and the malware month of the millennium.
According to Carnegie Mellon’s Cert Coordination Center (CERT/CC) the number of incidents of Internet Malware rose as;
- 1988 (6) The Morris Worm
- 2002 (82,094)
- 2003 (first half : 76,404)
- Mi2g (Mi2g.com) estimates US$32.8 billion in damages for August 2003 alone, with the W32/Blaster (Aug 11, a Windows DCOM RPC worm) and SoBig (Aug 18, an SMTP mass mailing worm).
- According to vunet.com, SoBig at its peak accounted for nearly 75% of all email traffic on the Internet, and caused an estimated US$1462 billion of damages (Mi2g SIPs database).
2003 - Sapphire worm virus (Slammer)
To Feb 2003, the Sapphire Worm was the fastest computer worm in history: A computer worm is a self-replicating malware computer program that uses a computer network to send copies of itself to other nodes (computers on the network) and it may do so without any user intervention Computer Worm (2010)[9].
- doubling in size every 8.5 seconds.
- infecting more than 90 percent of vulnerable hosts within 10 minutes.
- began to infect hosts around 05:30 UTC on Saturday, January 25.
- exploited a buffer overflow vulnerability in computers on the Internet running Microsoft’s SQL Server or MSDE 2000 (Microsoft SQL Server Desktop Engine). This weakness in an underlying indexing service was discovered in July 2002; Microsoft released a patch for the vulnerability before it was announced.
- The worm infected at least 75,000 hosts, perhaps considerably more, and caused network outages and such unforeseen consequences as canceled airline flights, interference with elections, and ATM failures. Several disassembled versions of the source code of the worm are available.
- Propagation speed was Sapphire’s novel feature: in the first minute, the infected population doubled in size every 8.5 (±1) seconds. The worm achieved its full scanning rate (over 55 million scans per second) after approximately three minutes, after which the rate of growth slowed down somewhat because significant portions of the network did not have enough bandwidth to allow it to operate unhindered.
- By comparison, it was two orders magnitude faster than the Code Red worm, which infected over 359,000 hosts on July 19th, 2001, with a leisurely doubling time of about 37 minutes.
- While Sapphire did not contain a malicious payload, it caused considerable harm simply by overloading networks and taking database servers out of operation. Many individual sites lost connectivity as their access bandwidth was saturated by local copies of the worm and there were several reports of Internet backbone disruption (although most backbone providers appear to have remained stable throughout the epidemic).
- It is important to realise that if the worm had carried a malicious payload, had attacked a more widespread vulnerability, or had targeted a more popular service, the effects would likely have been far more severe.
- Though very simple, Sapphire represents a significant milestone in the evolution of computer worms.
Virus Hoax
Along with real viruses there are many email virus hoaxes that circulate. Indeed the virus here is that if this is forwarded by many users it can impact on the performance of the mail servers!! Semantic (2007) [10] described the following hoax virus:
Subject: Virus Alert VIRUS WARNING To ALL INTERNET USERS: Virtual Card for You A new virus has just been discovered that has been classified by Microsoft (www.microsoft.com) and by McAfee (www.mcafee.com) as the most destructive ever! This virus was discovered yesterday afternoon by McAfee and no vaccine has yet been developed. This virus simply destroys Sector Zero from the hard disk, where vital information for its functioning are stored. This virus acts in the following manner: It sends itself automatically to all contacts on your list with the title "A Virtual Card for You". As soon as the supposed virtual card is opened, the computer freezes so that the user has to reboot. When the ctrl+alt+del keys or the reset button are pressed, the virus destroys Sector Zero, thus permanently destroying the hard disk. Please distribute this message to the greatest number of people possible. Yesterday in just a few hours this virus caused panic in New York, according to news broadcast by CNN www.cnn.com). This alert was received by an employee of Microsoft itself.
..and another one (circulating August 2011), it was displayed in a very large font in the email. If it is sent to enough users it is also useful for harvesting emails by spammers.
Sent: Wednesday, July 27, 2011 11:15 AM Subject: FW: Serious Threat ____________________________________________________ PASS THIS ON! IF A PERSON CALLED SIMON ASHTON ( SIMON25@HOTMAIL.CO.UK ) CONTACTS YOU THROUGH EMAIL DON'T OPEN THE MESSAGE. DELETE IT BECAUSE HE IS A HACKER!! TELL EVERYONE ON YOUR LIST BECAUSE IF SOMEBODY ON YOUR LIST ADDS HIM THEN YOU WILL GET HIM ON YOUR LIST.. HE WILL FIGURE OUT YOUR ID COMPUTER ADDRESS, SO COPY AND PASTE THIS MESSAGE TO EVERYONE EVEN IF YOU DONT CARE FOR THEM AND FAST BECAUSE IF HE HACKS THEIR EMAIL HE HACKS YOUR MAIL TOO!!!!!...... Anyone-using Internet mail such as Yahoo, Hotmail, AOL and so on. This information arrived this morning, Direct from both Microsoft and Norton. Please send it to everybody you know who has access to the Internet. You may receive an apparently harmless e-mail titled 'Mail Server Report' If you open either file, a message will appear on your screen saying: 'It is too late now, your life is no longer beautiful.' Subsequently you will LOSE EVERYTHING IN YOUR PC, And the person who o sent it to you will gain access to your name, e-mail and password. This is a new virus which started to circulate on Saturday afternoon. AOL has already confirmed the severity, and the anti virus software's are not capable of destroying it . The virus has been created by a hacker who calls himself 'life owner'.. PLEASE SEND A COPY OF THIS E-MAIL TO ALL YOUR FRIENDS, And ask them to PASS IT ON IMMEDIATELY! Take Care
Prevention
- Passwords
- The 25 worst passwords of 2011: ‘password,’ ‘123456′ (McKendrick, 2011)[11](in order)
- password, 123456, 12345678, qwerty, abc123, monkey, 1234567, letmein, trustno1, dragon
- baseball,111111,iloveyou,master, sunshine, ashley, bailey, passw0rd, shadow, 123123
- 654321, superman, qazwsx, michael, football
- Most common "business" password = "Password1" (exceeds 8 characters, has an uppercase letter and a number). Mar 5, 2012 goo.gl/GoZOA
- The 25 worst passwords of 2011: ‘password,’ ‘123456′ (McKendrick, 2011)[11](in order)
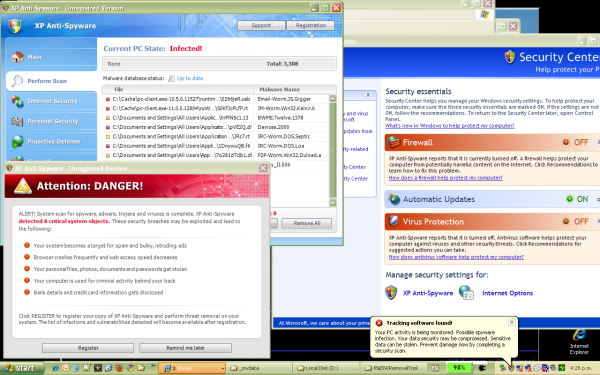
Spyware
Spyware is a significant security threat for Internet users. There are various types of spyware programs (see Table 1) creating serious problems such as copying and sending personal information, consuming CPU power, reducing available bandwidth, annoying users with endless pop-ups, and monitoring users computer usage.
Instructions to remove are in my blog: http://www.virtualmv.com/blog/index.php/2011/03/07/xp-antivirus-malware/
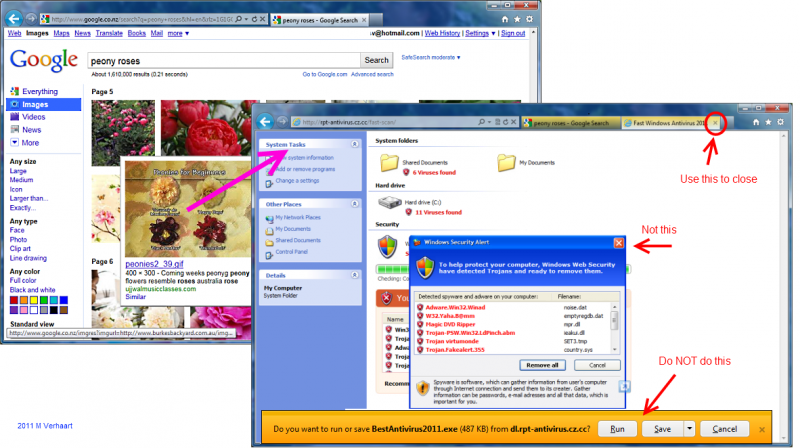
Trojan Example (Search engine poisoning)
In the example following, a link in Google images takes you to an Interactive Web page for AntiVirus2011 that supposedly checked your system, found viruses and automatically started the download of the spyware program BestAntiVirus2011.exe
- In May 2011 More than 113 million Internet users were redirected to malicious pages due to search engine poisoning(Trend Micro).
- How its done
- Hackers write code fooling search engines into giving fake results, while search engine companies try to write code to block the hackers.
- Hackers start by gaining access to legitimate Web sites and installing programs that monitor Google Trends for hot keywords.
- The program then searches for content related to the hot topics and uses the material to automatically generate new Web content of its own.
- As Google's bots roam the Web, the malicious program identifies them and feeds them the content from the fake Web pages. Since everything on the malicious site has be specifically chosen to relate to a search topic, the fake Web page and "poisoned" images will usually appear near the top of the relevant search results.
- When the user clicks on the thumbnail of the photo they want, the browser requests the page the image came from, but the malicious program redirects the user to a fake antivirus Web site, encouraging the user to buy unnecessary antivirus software.
- (Hecht, 2011, August 28)[12]
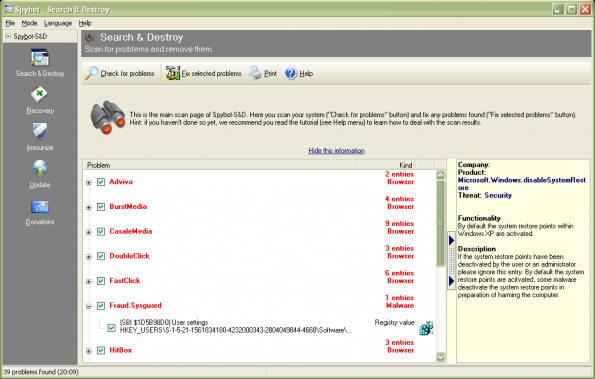
Antispyware solutions
- Anti-spyware law enforcement and legislation - USA (check http://thomas.loc.gov/)
- Internet Spyware (I-SPY) Prevention Act 2004
- SPYBLOCK Act
- Securely Protect Yourself against Cyber Trespass Act (SPY ACT)
- Anti-spyware systems
- Spybot Search and destroy http://www.safer-networking.org
- Spy sweeper http://www.webroot.com
- Ad-Aware http://www/lavasoftuse.com
Reference : (Lee & Kozar, 2005, August)[13]
Identity theft
Techniques
(Brody, Mulig, & Kimball, 2007)[14]
Phishing
Spear phishing
- Targets the person rather than the machine. Individual customised emails designed to get you to tell the scammer your userids and passwords. May appear to be from colleagues.
Spear phishing scams are rapidly spreading, one of the latest examples being a recently disclosed attempt to steal hundreds of accounts on Google's Gmail system and monitor the accounts of many prominent users. Security experts say that these efforts, which utilize fake emails that are personalized for the intended victim, are far more sophisticated than standard spear phishing initiatives, and thus are harder for recipients to spot. Symantec says that spear phishers' most popular targets are government agencies and senior managers and executives. To deter such attacks, Google encourages people to employ a two-step process that transmits a special code to their mobile phone when they log into Gmail. Meanwhile, the U.S. Defense Department asks staff to use a digital signature on their emails to authenticate their identity. However, West Point computer security expert Lt. Col. Gregory Conti warns that spear phishers have the advantage of momentum, given that their forgeries can be realistic and very subtle. He says that one reason the problem is getting harder to counter is that fraudsters are using social networks to amass personal information about potential targets. (Richtel, Kopytoff, & Markoff, 2011, June 02)[15]
Examples
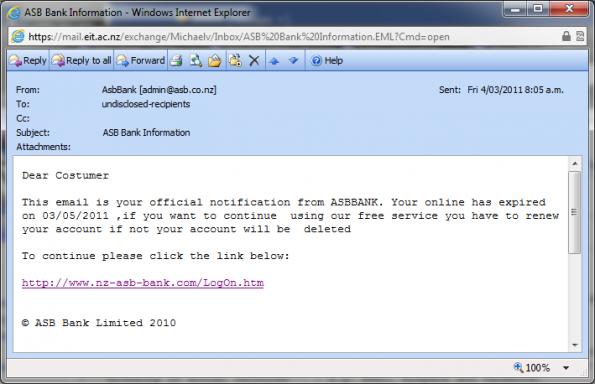
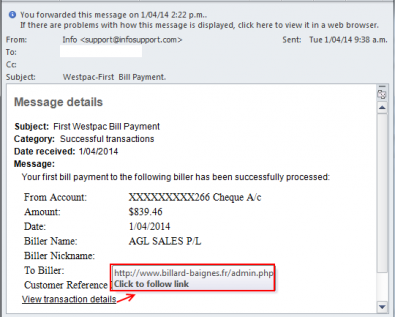
A very clever phishing email.. notice the URL in the "View transaction details" it will link to what appears to be the Westpac login screen
|
Admin Notices MKS KHADARI [khadari@xxxx.co.in] Wednesday, 7 September 2011 3:46 a.m. Attention: Webmail User, This mail was send by Admin Center to notify you that we have temporally prevented access to your account. We have reasons to believe that your account may have been accessed by someone else and it was for illegal activities. Please run this file and Follow instructions: You are to send Admin Center the information below otherwise we shall block this account permanently, you must reply to this email immediately and enter your details below. Name: Login: Password: Note that if we do not receive your reply in the next 48hrs we shall deactivate this account. "Admin Center Support Team" Copyright © web Admin 2011 All Rights Reserved.
This email has been scrubbed for your protection by SecureMX. For more information visit securemx.in
|
| This very basic phishing email I received in September 2011, that amazingly avoided the spam filters. |
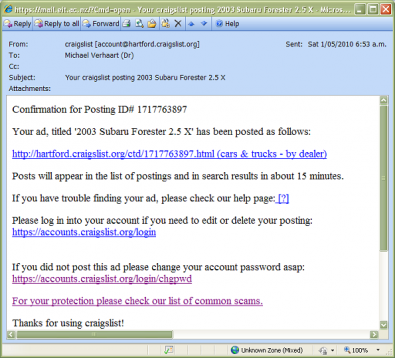
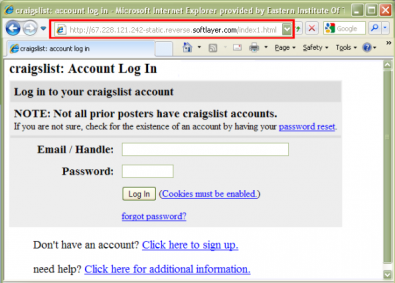
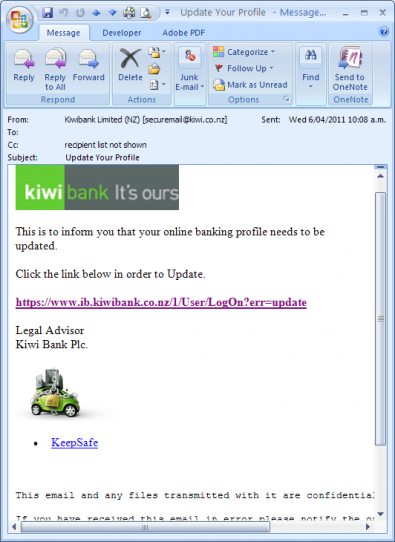
The following example is a very clever phishing email. It indicates you have made a purchase and wants you to cancel it using your login/password. All of the links go to the page shown in the browser, however notice the url (shift+click to enlarge images).
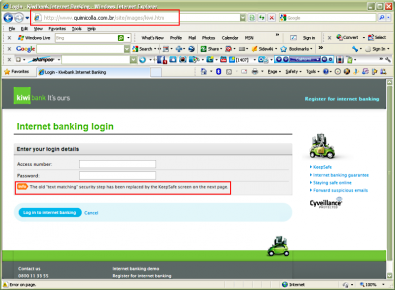
This example is more typical of an email/banking scam. Note the URL and how they cleverly change the security method on the following screen
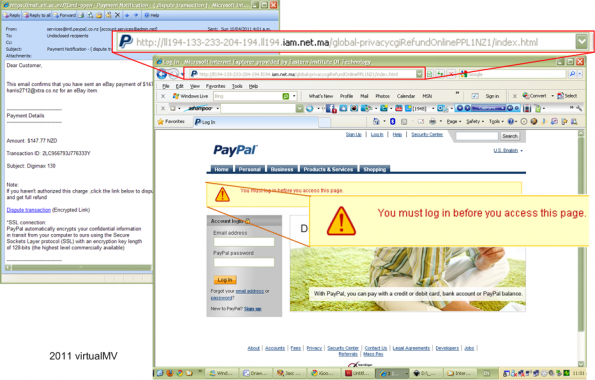
This example of a Phish email links to fake PayPal page (note URL). User must login to activate the page (all the hyperlinks were not working)
Types
Source: (Identity theft, 2009)[16]
Identity theft - Prevention
- Secure any information that may be used to identity you. eg: birth certificates, drivers license, Passport and photo identification.
- Lock your letterbox. Mail can be used as proof of address
- Buy antivirus and antispyware software from a reputable vendor for your computer, and update regularly.
- Avoid giving personal information over the phone
- Shred or burn bank and credit card statements before disposing of them.
- Be careful how much information is shared on social network sites. This is an easy way to obtain information about a person. Make sure you understand the security settings.
- Be careful when opening email check the sender if unknown do not open it.
From report by Matairangi, R.(2007)
Fraud
What is fraud?
Criminal deception, use of false representations. E.g. Using Credit card numbers (Sengstack, 2000, Sep)[17].
1998 - Teens use internet for credit-card fraud
Teenagers are going on spending sprees of up to $150,000 using credit card numbers generated from free software found on the Internet. Parents are using their 13 and 14 year old siblings to generate the numbers using their home computers since they know they can’t be prosecuted. Teenagers were being paid $5 for an A4 sheeet of valid credit-card numbers. The downloadable package was simple to use. The first step was to get hold of a legitimate credit card number. Fraudsters usually only used one number at a time. Technical Investigator Janice Mockridge said last week (Jun ’98) a warrant was issued for an Auckland woman who within days of being seen by police committed a $15,000 fraud to pay for her degree ("Teens use internet..", 1998, Jun 9)[18]
Basic controls
- Keep your browser updates current.
- Run current anti-virus software. (This means keeping updates current).
- Check security updates and patches on Microsoft`s web site (In Windows 98, Me and XP use Windows Update)
- Use a firewall
- e.g. ZoneAlarm ( http://www.zonelabs.com )- a free personal firewall.
- Unless needed remove File & Printer Sharing for MS Networks under Network Control panel
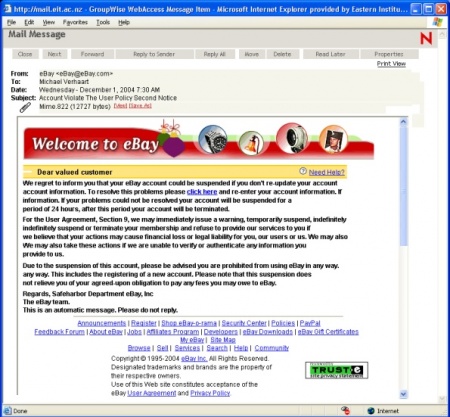
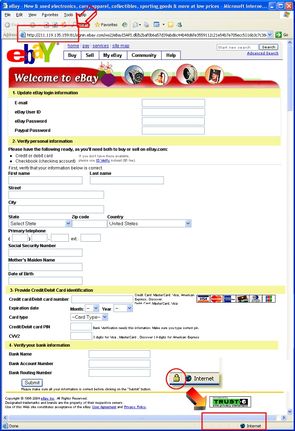
2004: eBay email fraud
Click on the images to zoom. Notice
- "extra" numbers in front of the URL and
- Lack of padlock in IE message bar
2007: eBay fraud: Boy racers catch dumb blonde fraudster
A BOARD devoted to boy racers has done a sterling job outing a woman who tried to con one of its number out of cash for a Wii. One of the regulars of the Scoobynet.com board paid £180+£30 for a Wii from eBay and when it didn't turn up he contacted the seller, Miss Hightee H. Butzlaff. She told him that he could call the cops if he wanted too, but she didn't live in the UK so ner. While many people would have thought that Hightee H. Butzlaff was a joke name, the buyer had managed to get some of her personal details including her phone number, and address. He handed over the details to the group who promply had a field day with it. The denizens of Scoobynet did as much searching as they could on the woman. They found pictures of her in her underwear, hobbies, religion. Apparently, Hightee started to feel a bit less cocky and offered to remove the pictures if she refunded the money. But it is starting to look like the horse has well and truly bolted and the boy racers cannot be stopped. They have even built her a website where the story is told. The message seems to be if you are an attractive Dutch blonde with an interest in earning some cash on the side through ebay scamming, it pays not to use your real name and address
A separate discussion board has been set up to catch the scammers in the UK The Scam Busters (n.d.) Retrieved December 04, 2007 from http://www.thescambusters.co.uk/
(Farrell, 2007)[19] and related sites http://www.highteebutzlaff.co.uk/
Hacking
Internet Hacking
While connected to the internet your PC is open to the global network. Hackers can and do hack into personal/home PCs, often installing software that will capture passwords and any other "sensitive" data you may have on your PC. Criminal hacking range from obnoxious to destructive. Hackers uses tools to locate an IP address, which may be assigned by your ISP during each dial-up session or static, often used when connecting using high speed connections like DSL. Once the IP address is identified hackers search for open ports. Web access on a PC is typically port 80, while FTP runs through port 21. Users may also be tricked into running malicious software through a "Trojan" horse. This may be software attached to an email. "Back-Orifice" is probably the best known Trojan and open ports that allows a hacker to attack your system.
Reference : (Sengstack, 2000, Sep) [20]
2000 Hacking into & using somebody else’s Internet account.
On changing to a free ISP, and changing the unlimited (pay for) xtra account to per hour, an xtra user discovered hacker was stealing hundreds of dollars of time, and had run up nearly $800 before discovery. Xtra wanted to charge a further $200 to investigate!. (Foreman, 2000, Aug 23) [21]
Lets talk Wordpress Security.
WordPress is one of the most popular blog platforms on the market today. Many bloggers use it because it free, easy to use, and offers endless options to customize and optimize the experience of website visitors. Since the platform is so popular, it is expected that hackers would also be interested in it as well.
Wordpress, a popular blog platform, being utilised at educational institutions (including EIT) is free, easy to use and also susceptible to hacking. Find out about Wordpress security and what can be done to make Wordpress more secure. Tazzy 07/09/2011
http://fearlessflyer.com/2011/08/lets-talk-wordpress-security/
Cyber-Terrorism
Gabriel Weimann (2005)[22] has identified eight specific behaviours that mainstream terrorist organisations use the Internet for; Brief descriptions of the behaviours follow:
- Psychological Warfare: Disinformation, dissemination of images, psychological fear, cyber terrorism fear, the nature, content, medium of the Internet is an advantage to cyber terrorism.
- Publicity and Propaganda: Control content, use multimedia, how perceived and how enemies are perceived, widespread publicity and propagation and dissemination of their perceived cause.
- Data Mining: Vast 'digital library' (one billion pages), intended targets and victims, counter terrorism measures and practices.
- Fundraising: Internet allows Cyber Terrorism and Terrorism to generate own funds and revenue, now using e-commerce websites for online donations and transactions.
- Recruitment and Mobilisation: Recruitment and mobilisation platform, find recruits-allow to contact 'Terrorist' organisation.
- Networking: Decentralised command structure, communication with each other, ideas, suggestions, techniques, Recruits advertise their availability to organisations.
- Sharing Information: 'The Terrorists Handbook', 'The Anarchist Cookbook', provide weapon information, technological advantage, Cyber terrorism and Terrorists have adopted and adapted to the evolution of the web.
- Planning and Coordination: Obtain components and share information, plan and coordinate operations.
Video Discussion on Cyber Terrorism
- Cyber Terrorism: http://www.youtube.com/watch?v=RaQCURNL5rQ
- CNN.com: Cyber-terrorism threat: http://www.youtube.com/watch?v=ICgpAkddfFY
- Exploitive (going where they shouldn't - stealing information)
- Disruption (fooling with someone else's network)
- Destruction (Create physical event - e.g. physical destruction of property)
(From a Research assessment Tazzy, 2011 )
Security and Data Protection in a Google Data Center
| Security and Data Protection in a Google Data Center |
Encryption and Decryption
- Encryption is the conversion of data into a form, called a cipher, that cannot be easily intercepted by unauthorized people.
- Decryption is the process of converting encrypted data back into its original form, so it can be understood.
The use of encryption/decryption is as old as the art of communication. In wartime, a cipher, often incorrectly called a "code," can be employed to keep the enemy from obtaining the contents of transmissions. (Technically, a code is a means of representing a signal without the intent of keeping it secret; examples are Morse code and ASCII.) Simple ciphers include the substitution of letters for numbers, the rotation of letters in the alphabet, and the "scrambling" of voice signals by inverting the sideband frequencies. More complex ciphers work according to sophisticated computer algorithms that rearrange the data bits in digital signals.
In order to easily recover the contents of an encrypted signal, the correct decryption key is required. The key is an algorithm that "undoes" the work of the encryption algorithm. Alternatively, a computer can be used in an attempt to "break" the cipher. The more complex the encryption algorithm, the more difficult it becomes to eavesdrop on the communications without access to the key. Encryption/decryption is especially important in wireless communications. This is because wireless circuits are easier to "tap" than their hard-wired counterparts. Nevertheless, encryption/decryption is a good idea when carrying out any kind of sensitive transaction, such as a credit-card purchase online, or the discussion of a company secret between different departments in the organization. The stronger the cipher -- that is, the harder it is for unauthorized people to break it -- the better, in general. However, as the strength of encryption/decryption increases, so does the cost.
In recent years, a controversy has arisen over so-called strong encryption. This refers to ciphers that are essentially unbreakable without the decryption keys. While most companies and their customers view it as a means of keeping secrets and minimizing fraud, some governments view strong encryption as a potential vehicle by which terrorists might evade authorities. These governments, including that of the United States, want to set up a key-escrow arrangement. This means everyone who uses a cipher would be required to provide the government with a copy of the key. Decryption keys would be stored in a supposedly secure place, used only by authorities, and used only if backed up by a court order. Opponents of this scheme argue that criminals could hack into the key-escrow database and illegally obtain, steal, or alter the keys. Supporters claim that while this is a possibility, implementing the key escrow scheme would be better than doing nothing to prevent criminals from freely using encryption/decryption.
Selected Links The Electronic Frontier Foundation has extensive information about encryption/decryption, along with the latest legal updates concerning the key-escrow issue. http://www.eff.org/
CAPTCHA: Machine un-readible text
- CAPTCHA (Completely Automated Public Turing test to tell Computers and Humans Apart)
An image with distorted text at the bottom of web registration forms. Used by Yahoo, Hotmail, Paypal and others to prevent automatic registration, and work because no computer program can currently read distorted text.
For further discussion ... http://en.wikipedia.org/wiki/CAPTCHA |
- GIMPY: A computer generated distorted text by getting 7 dictionary words, distorting them and asks the user to identify 3.
- BONGO: Named after M.M. Bongard who published a book of pattern recognition problems in the 1970s. Users are asked to solve a visual pattern recognition problem.
- PIX. A large database of labelled "concrete" images (like a hore, house, etc)is used where the user is able to identify them. [ http://inkblotpassword.com/ ]
Sound based CAPTCHAs. A distorted word is created as a sound clip.
An important accessibility issue here is that the CAPTCHAs (apart from the audio clip) uses visual image.
Reference : (von Ahn, Blum, & Langford, 2004, Feb)[23]
Restricting which pages are spidered : Robots.txt
Robots.txt Search engines will look in your root domain for a special file named "robots.txt" (http://www.mydomain.com/robots.txt). The file tells the robot (spider) which files it may spider (download). This system is called, The Robots Exclusion Standard. The format for the robots.txt file consists of records containing two fields : a User-agent line and one or more Disallow: lines. <Field> ":" <value> For example: The User-agent line specifies the robot.
User-agent: googlebot
or use the wildcard charcter "*" to specify all robots:
User-agent: *
A disallow directive is used to give instructions as to what cannot be spidered. For example;
Disallow: email.htm Disallow: michael #comment
(Note it is best to put comments on their own lines)
Other examples;
The following allows all robots to visit all files because the wildcard "*" specifies all robots.
User-agent: * Disallow:
This one keeps all robots out.
User-agent: * Disallow: /
The next one bars all robots from the cgi-bin and images directories:
User-agent: * Disallow: /cgi-bin/ Disallow: /images/
This one bans Roverdog from all files on the server:
User-agent: Roverdog Disallow: /
This one bans keeps googlebot from getting at the cheese.htm file:
User-agent: googlebot Disallow: cheese.htm
".. robots.txt is a voluntary mechanism," said Martijn Koster, a Dutch software engineer and the author of a comprehensive tutorial on the robots.txt convention (robotstxt.org). "It is designed to let Web site owners communicate their wishes to cooperating robots. Robots can ignore robots.txt."
Ref: (PHD Software Systems, 2002)[24]
2005 Keeper of Expired Web Pages Is Sued Because Archive Was Used in Another Suit
The Internet Archive, a searchable online repository of defunct Web sites and other multimedia content, has been targeted by a copyright infringement suit filed by Healthcare Advocates, which claims that access to its old Web pages in the archive was unlawful and unwarranted. Named as co-defendant in the suit is the firm of Harding Earley Follmer & Frailey, which searched the Internet Archive two years ago to unearth Healthcare Advocates’ old Web pages as material for their defense of Health Advocate, which the similarly named Healthcare Advocates was suing for trademark violation. The Internet Archive makes copies of publicly accessible sites periodically and automatically through the use of Web-crawling "bots," and then stores the copies on its servers for later retrieval using the Wayback Machine, the archive’s search tool. The latest lawsuit argues that Harding Earley representatives should not have been able to access the old Healthcare Advocates Web pages because the organization, shortly after filing the suit against Health Advocate, put a robots.txt file on its own servers that was supposed to tell the Wayback Machine to disallow public access to the historical versions of the site. The suit states that the Digital Millennium Copyright Act was breached when a member of Harding Earley requested old versions of Healthcare Advocates’ Web site hundreds of times using the Wayback Machine, and that in almost 100 instances the robots.txt failed to block the requests. The Internet Archive’s failure to honor the robots.txt file constitutes a breach of contract and fiduciary duty, according to the lawsuit. However, lawyer William F. Patry contends that such a contract does not exist because the robots.txt file is part of a wholly voluntary system (Zeller, 2005, Jul 13)[25].
eCommerce
e-Commerce security: Attacks and preventive strategies (Khusial, & McKegney, 2005)[26]
Security of business transactions
Security includes authenticating business transactors, controlling access to resources for registered or selected users, encrypting communications, and, in general, ensuring the privacy and effectiveness of transactions. Among the most widely-used security technologies are SSL and RSA (named after the men who invented it!). Secure Electronic Transactions (SET) is an emerging industry standard. One of the biggest challenges in the development of electronic commerce has been for banks and merchants to overcome the issues of customer identification and account verification for online purchases. While the credit card systems have a process in place to verify and authorize transactions, the Internet poses challenges for merchants to not only validate that funds are available in an account, but to positively identify that particular customer is in fact authorized to use that account for purchases.
Web site trust
Since 1998, Ranking.com has performed market research upon a statistically, geographically and demographically significant number of Internet surfers. By recording these surfers’ website visits, Ranking.com calculates the ranking for the top 900,000 (growing every month) most visited websites and provides these results to surfers absolutely FREE for all its services!
EMERgency24 (2005) Free Internet Traffic Ranking of the Top 900,000 Most Visited Popular Web Sites. Retrieved February 24, 2005 from http://www.ranking.com/
Transferring money
Digital certificates
The solution to customer identification and account verification for online purchases are digital certificates which are electronic "credit cards" that establishes your credentials. It is issued by a certification authority (CA). It contains your name, a serial number, expiration dates, a copy of the certificate holder’s public key (used for encrypting and decrypting messages and digital signatures), and the digital signature of the certificate-issuing authority so that a recipient can verify that the certificate is real.
Secure Electronic Transactions (SET) and Account Authority Digital Signatures (AADS)
The SET protocol (Secure Electronic Transactions) was proposed in 1995, but it has not been implemented yet due to a number of perceived flaws. More recently, there has been a standard proposed called x9.59 (Account Authority Digital Signatures, or AADS), which solves some of these problems. In particular, it calls for banks to be the certification authority for their own customers. This should reduce the possibility of fraud since certification is not trusted to another company and since both physical cards and digital certificates can be cancelled at the same time.
Secure Sockets Layer (SSL)
SSL is the de-facto standard for managing the security of message transmissions in a network. It was created by Netscape who have proposed it as an Internet standard. Essentially it encrypts your personal information (credit card number, name and address etc.) when it is sent across the Internet to the on-line shop and then unencrypts the information again at the other end. The system is based on the public-key private-key encryption system (see Diagram). The programming for keeping messages confidential is contained in a program layer between the application (e.g. the Web browser) and the Internet’s TCP/IP layers. (The "sockets" part of the term refers to the sockets method of passing data back and forth between a client and a server program in a network or between program layers in the same computer). SSL uses the public-and-private key encryption system from RSA, which also includes the use of a digital certificate. The client part of SSL is included in any Netscape web browser. The server part of SSL is included in all Netscape servers, while other companies’ servers can also be SSL enabled by using Netscape’s SSLRef program library.
Fears
Many businesses and consumers are wary of conducting business over the Internet. While consumers are concerned about security and privacy issues, businesses are concerned about the lack of a predictable legal environment governing transactions. Issues such as enforcement of contracts, liability, intellectual property protection, security and other matters have caused businesses to be cautious.
In 2006 Due to the low uptake of internet banking customers Westpac Bank introduced a 100% money back guarantee as follows "In the unlikely event that you fall victim to online fraud as a result of using Westpac New Zealand's online banking service, we will always reimburse, in full, all money taken from your account." ( http://www.westpac.co.nz/olcontent/olcontent.nsf/Content/Online+banking+guarantees ) - woodstockworld 07/09/2011)
As use of the Internet expands, governments may try to impose extensive regulations on the Internet and electronic commerce. Potential areas of problematic regulation include taxes and duties, restrictions on the type of information transmitted, control over standards development, licensing requirements and rate regulation of service providers. There will be a lot of hard decisions for world politicians to make in the next few years, but hopefully widespread competition and increased consumer choice will be the defining features of the new digital marketplace.
 References
References
- ↑ Sophos (n.d.) Data security toolkit. Retrieved March 7, 2011 from http://www.sophos.com/lp/threatbeaters-dp/download-toolkit/download.html
- ↑ (2014, May 22.eBay hacked, massive data theft suspected, In HZ Herald. Retrieved from http://www.nzherald.co.nz/business/news/article.cfm?c_id=3&objectid=11259488
- ↑ Honorof, M., (2013) Website Shows Cyberattacks as They Happen. Retrieved from http://mashable.com/2013/03/08/website-shows-cyberattacks/
- ↑ 4.0 4.1 Jackson, K. (2009) Web Security – Napier. Retrieved June 3, 2009 from http://pageofwords.com/blog/2009/05/28/WebSecurityNdashNapier.aspx
- ↑ Guya.net (2009) Malicious camera spying using ClickJacking. Retrieved June 3, 2009 from http://blog.guya.net/2008/10/07/malicious-camera-spying-using-clickjacking/
- ↑ Jackson (2010). Kirk Jackson's Page of Words. Retrieved September 16, 2010 from http://pageofwords.com/blog/CategoryView,category,Security.aspx
- ↑ Sobig (computer worm). (2010, September 1). In Wikipedia, The Free Encyclopedia. Retrieved 20:04, September 16, 2010, from http://en.wikipedia.org/w/index.php?title=Sobig_(computer_worm)&oldid=382207916
- ↑ Blaster (computer worm). (2010, September 15). In Wikipedia, The Free Encyclopedia. Retrieved 20:03, September 16, 2010, from http://en.wikipedia.org/w/index.php?title=Blaster_(computer_worm)&oldid=384967677
- ↑ Computer worm. (2010, September 14). In Wikipedia, The Free Encyclopedia. Retrieved 19:59, September 16, 2010, from http://en.wikipedia.org/w/index.php?title=Computer_worm&oldid=384764599
- ↑ Symantic (2007) Virtual Card for You. Retrieved September 4, 2007 from http://www.symantec.com/security_response/writeup.jsp?docid=2001-011015-3610-99&tabid=2
- ↑ McKendrick, J. (2011, Nov 18) The 25 worst passwords of 2011: ‘password,’ ‘123456′. ZDNet (SmartPlanet) CBS. Retrieved from http://www.smartplanet.com/blog/business-brains/the-25-worst-passwords-of-2011-8216password-8216123456-8242/20065?tag=nl.e098
- ↑ Hecht, J. (2011, August 28) Image searches 'poisoned' by cybercriminals. New Scientist Retrieved from http://www.newscientist.com/article/mg21128276.500-image-searches-poisoned-by-cybercriminals.html
- ↑ Lee, Y.,& Kozar, K.A. (2005, August) Spyware: Investigating factors affecting the adoption of anti-spyware systems . Communications of the ACM, Volume 48 Issue 8 , pp72-77, ACM Press
- ↑ Brody, R.G., Mulig, E., & Kimball, V. (2007). Phishing, Pharming and Identity Theft, Academy of Accounting and Financial Studies Journal, 11, 43-57.
- ↑ Richtel, M.,; Kopytoff, V.G., & Markoff, J. (2011, June 02) E-Mail Fraud Hides Behind Friendly Face. New York Times
- ↑ Identity theft. (2009, September 21). In Wikipedia, The Free Encyclopedia. Retrieved September 21, 2009, from http://en.wikipedia.org/w/index.php?title=Identity_theft&oldid=314454416
- ↑ Sengstack, J. (2000, Sep) Make your PC hacker-proof, NZ PC World No. 131, pp 82-88.
- ↑ Teens use internet for credit-card fraud (1998, Jun 9). , The Hawke`s Bay Herald Tribune p3.
- ↑ Farrell, N. (2007) Boy racers catch dumb blonde fraudster. Retrieved December 04, 2007 from http://www.theinquirer.net/gb/inquirer/news/2007/12/03/boy-racers-catch-dumb-blonde
- ↑ Sengstack, J. (2000, Sep) Make your PC hacker-proof. , NZ PC World No. 131, pp 82-88.
- ↑ Foreman, M. (2000, Aug 23) Dollar-saving plan flushes out hacker. User claims xtra not sympathetic. , NZ Herald, pg A2
- ↑ Weiman, G. (2005). How Modern Terrorism Uses the Internet. The Journal of international Security Affairs (8), 1. Retrieved from http://www.usip.org/publications/wwwterrornet-how-modern-terrorism-uses-internet
- ↑ von Ahn, L., Blum, M. & Langford, J. (2004, Feb) Telling humans and computers apart automatically. Communications of the ACM, Volume 47 Issue 2 ISSN:0001-0782 , pp 57-60
- ↑ PHD Software Systems (2002) Robots.txt Tutorial Retrieved July 18, 2005 from http://www.searchengineworld.com/robots/robots_tutorial.htm
- ↑ Zeller, T. Jr. (2005, Jul 13) Keeper of Expired Web Pages Is Sued Because Archive Was Used in Another Suit. Retrieved July 18, 2005 from http://www.nytimes.com/2005/07/13/technology/13suit.html
- ↑ Khusial, D. & McKegney, R. (2005) e-Commerce security: Attacks and preventive strategies. Retrieved from http://www.ibm.com/developerworks/websphere/library/techarticles/0504_mckegney/0504_mckegney.html
|
virtualMV | Superquick wiki guide | Please give me some feedback |
Internet & Web development (2)/Course materials/Web Site Issues/Security. (2024). In WikiEducator/VirtualMV wiki. Retrieved December 22, 2024, from http:https://wikieducator.org/Internet_%26_Web_development_(2)/Course_materials/Web_Site_Issues/Security (zotero)
|