File Management and Protection/Data Protection/Privacy issues
| File Management and Protection | |
|---|---|
| Data Protection | Introduction | Information security | Privacy issues | Backup techniques | Computer viruses | Key points | Assessment |
Privacy issues
Information stored on computers
All computers from laptop computers to mainframes contain information. Much of this, whether corporate or personal, is confidential. Many thousands of laptop computers containing important company or State information have been stolen. Since most corporate records are now kept in electronic form on computer systems, procedures need to be put in place to protect the computers.
Apart from deliberate violations by people, computers are also subject to accidental damage and natural disasters.
Physical procedures
Physical access to mainframes should be restricted to operators and systems administrators. Facilities should be fire and flood proof. Highly sensitive installations should also have adequate protection from criminal and terrorist activities.
Desktop and laptop computers are very vulnerable to theft. A simple procedure is to only allow authorised people access to offices. The use of security cameras can also act as a deterrent. Desktop computers can be physically attached to the floor or a work surface.
Laptop computers present the greatest risk. They are not only light and easy to pick up, but they are also more expensive and valuable than desktops. The best protection is not to let them out of site. If a manager is staying at a hotel, he or she can leave the computer in the hotel safe rather than their room.
Software procedures
Information can be stolen, altered or deleted without the computer being physically removed. The information may even be accessed across the Internet.
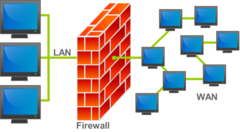
Firewalls
A firewall is the first line of defence against hackers. It is a computer program that is installed on a computer that connects a network to the Internet. The firewall analyses the packets that pass in and out of the network. It is programmed to follow certain rules which enable it to decide whether or not to allow a packet to pass. There is firewall software available that can be installed on a stand-alone PC.
Access rights
Access rights can refer to both physical and software. In a physical sense, these refer to different members of staff who have to gain physical access to certain areas. For example, access to the room containing the mainframe may be restricted to operators. Software rights refer to the level of access different users have to different levels of data and information. For example, some users may have no access to certain data, others may only be able to read the data but not change it. Others in turn may have full rights to create and change data. Access rights are associated with a user id and password. A user id could be a user name or a combination of letters and numbers. To log on to a system a user would need a user id and a password. As other users may know the user id of colleagues, another level of security in terms of passwords needs to be added. Passwords are private and should never be divulged to anyone else. Users could have several user ids, each with a different level of security. They would log on each time with the lowest level of security they need to accomplish a given task.
Password policies
Password policies refer to guidelines or requirements on the structure and use of passwords. They can be required for access to a computer system or a group of files or a single file. The following are some guidelines for password policies:
- They should never be blank
- They should not be the names of family members or pets or anything else that would be easy for an intruder to try out
- Ideally they should never be words, especially words like administrator, admin or root
- They should never be less than five characters and preferably longer. Short passwords can easily be determined by a brute force password cracker. This is a piece of software that repeatedly feeds in all combinations of letters and numbers until access is gained. With short passwords this can be done in seconds
- A good policy is to use a meaningless combination of letters and numbers that is seven or eight characters long. What some users do is to take a meaningful word such as looking and replace the o with the number 0 and the letter i with the number 1 so that the password becomes l00k1ng. You could also make a less obvious change, for example replace k with 3 and g with 9 so that the password becomes loo3in9
- Passwords should be changed on a regular basis. Administrators can set a policy that automatically causes passwords to expire after a certain period of time, for example 7 days
- When using a PC, you would need to use an operating system that provides genuine access protection with a user id and password.